


The article presents a comprehensive framework for conducting a purchase product security audit in Mexico, underscoring its critical role in identifying vulnerabilities, ensuring regulatory compliance, and enhancing overall security measures. By outlining essential steps such as:
the article demonstrates how a systematic approach can significantly improve procurement processes. This not only protects organizations from potential risks but also mitigates regulatory penalties, reinforcing the necessity of diligent security audits in today's complex landscape.
A purchase product security audit in Mexico stands as a crucial safeguard against vulnerabilities in the procurement process, particularly in a landscape where fraud attempts are alarmingly prevalent. Organizations that engage in this thorough evaluation not only enhance their compliance with complex regulations but also bolster their overall security posture.
However, the challenge lies in navigating the intricate web of regulatory requirements and preparing adequately for the audit process.
How can organizations ensure they are not only compliant but also proactive in addressing potential risks?
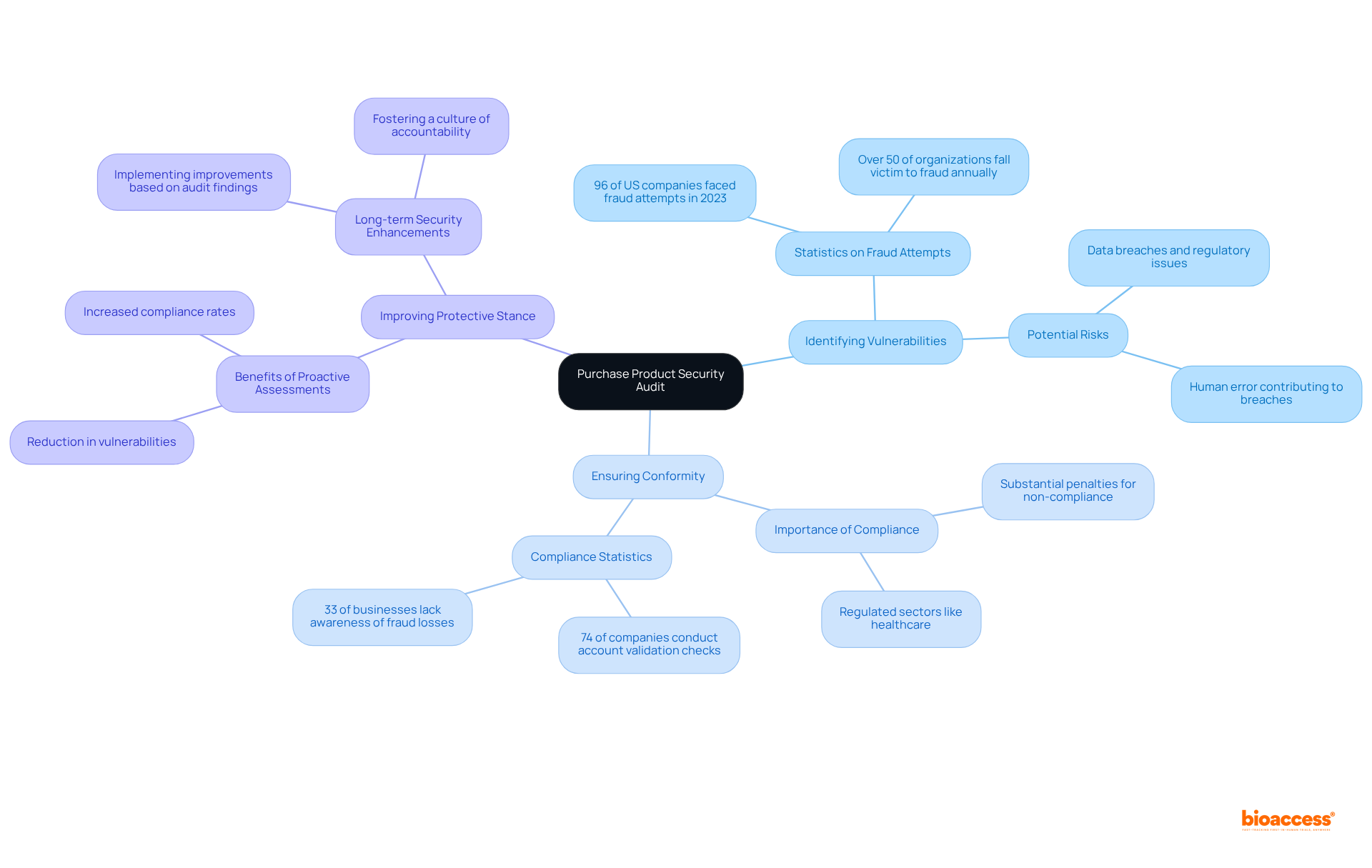
A purchase product security audit in Mexico is paramount for assessing the security measures that govern the procurement process of products. This critical examination identifies potential vulnerabilities that could lead to data breaches or regulatory issues. By grasping the significance of the purchase product security audit in Mexico, organizations can strategically prepare for subsequent actions, ensuring compliance with local regulations while safeguarding their assets and reputation. The key objectives include:
The impact of security evaluations on organizational compliance is profound. Regular assessments not only help in identifying gaps but also foster a culture of accountability and integrity within procurement teams. Notably, a significant number of firms remain unaware of their losses stemming from procurement fraud, which highlights the critical need for a purchase product security audit in Mexico to uncover hidden risks. By prioritizing security evaluations, organizations can navigate the complexities of procurement with heightened confidence and resilience.
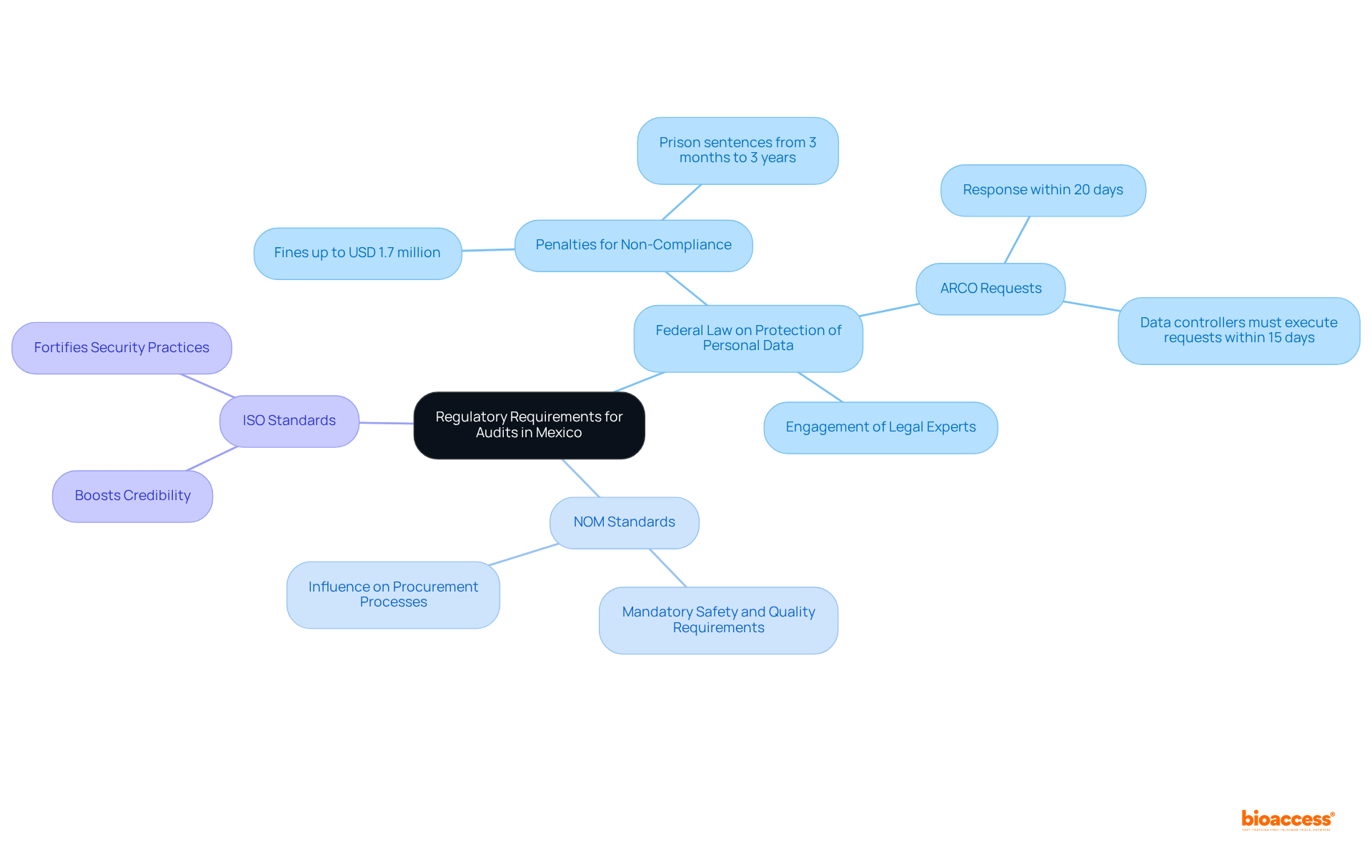
In Mexico, organizations must navigate a complex regulatory environment to successfully conduct a purchase product security audit Mexico. Key regulations include:
Organizations are encouraged to engage legal experts or compliance officers to fully understand and implement all applicable regulations. This is especially crucial in light of the recent changes introduced by the new law enacted on March 20, 2025, and the implications of the extinction of INAI as of May 2025, which may affect compliance strategies.
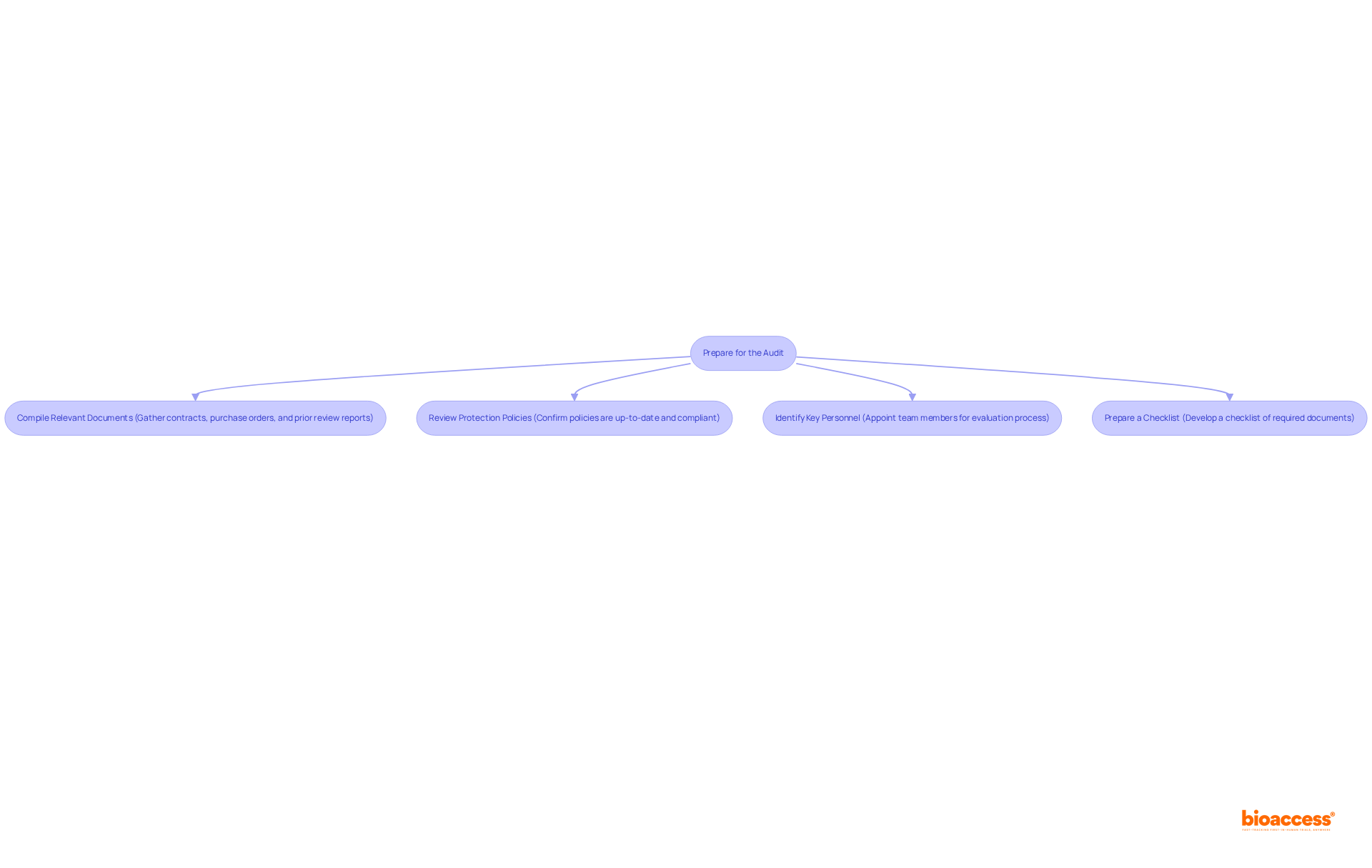
Preparing for a purchase product security audit in Mexico requires meticulous collection of essential documentation and resources, a critical component for an effective review process. Key steps include:
By being well-prepared for a purchase product security audit in Mexico, organizations can facilitate a smoother review, enabling them to swiftly address any issues that may arise and ultimately bolster their security posture. Furthermore, organizations should anticipate potential challenges in the evaluation, such as complex IT systems and emerging cyber threats, which could impact the review's effectiveness. After gathering documentation, it is advisable to conduct a self-evaluation or arrange for an assessment to confirm readiness.
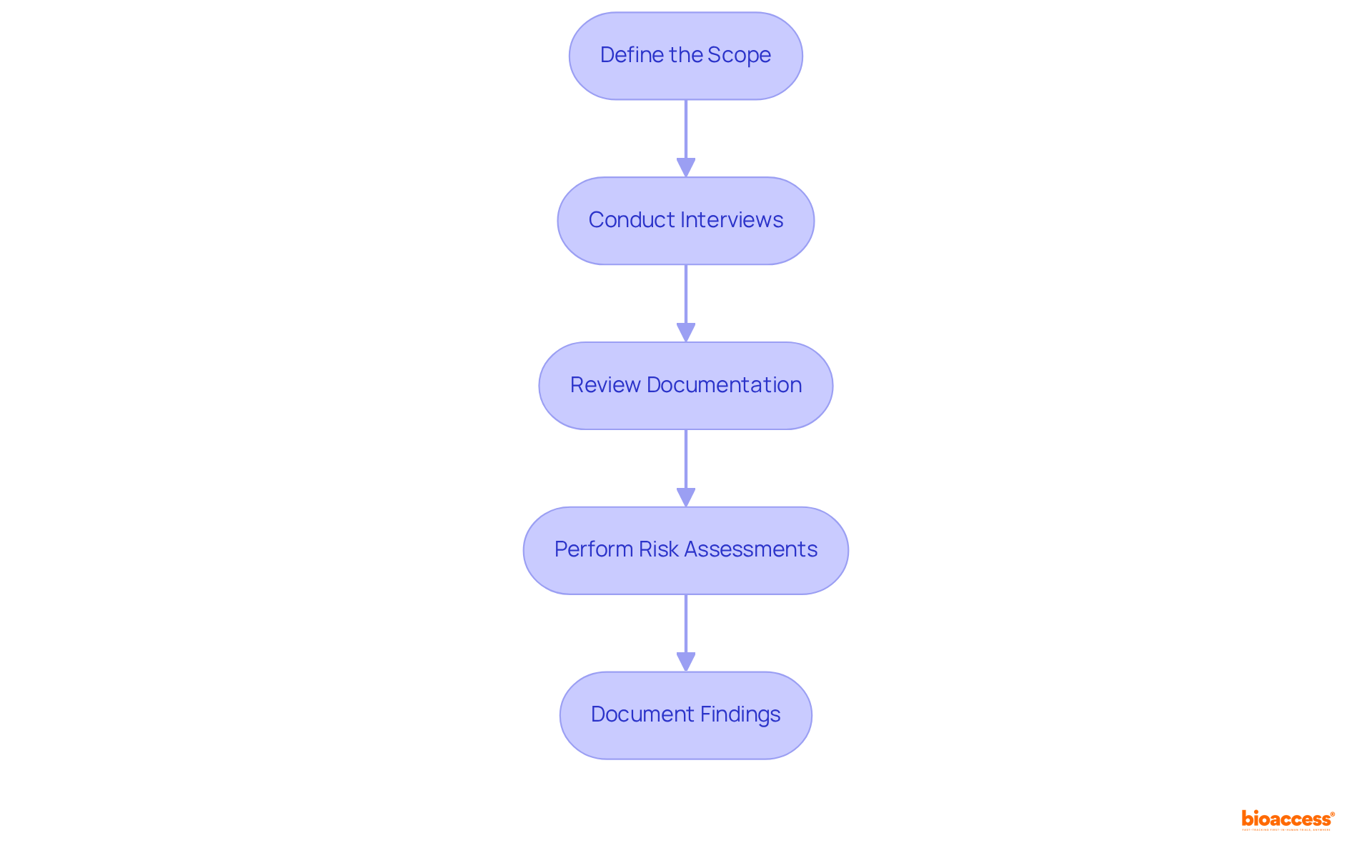
Conducting a purchase product security audit in Mexico involves several key steps to ensure thoroughness and accuracy. This step-by-step guide is essential for organizations aiming to enhance their procurement processes:
Define the scope: Clearly outline the specific aspects of the procurement process that will be audited. This initial step is crucial, as it sets the parameters for the audit and ensures that all relevant areas are covered. A well-defined scope helps auditors focus on critical vulnerabilities, such as compliance gaps and supplier reliability issues. As noted by industry experts, "The most important aspect of risk assessment is the initial identification of potential risks."
Conduct interviews: Engage with key personnel involved in the procurement procedure to gather insights and identify potential issues. These discussions can expose shared weaknesses, such as insufficient supplier evaluation, which almost half of executives link to manual methods. Furthermore, a quarter of business executives admit they are not vetting their suppliers properly, highlighting the severity of this issue.
Review documentation: Examine all gathered documents for conformity with regulations and internal policies. This includes contracts, purchase orders, and supplier agreements. Efficient contract management software can optimize this procedure, ensuring that all documents are current and accessible. Utilizing such software can help ensure accurate contract writing and compliance tracking.
Perform risk assessments: Identify and evaluate risks associated with the procurement process. This step is essential for understanding potential threats, such as supply chain disruptions or vendor price creep, which can lead to unexpected costs. Recent case studies have shown that proactive risk management strategies, like diversifying suppliers, can mitigate these impacts and enhance overall security posture.
Document findings: Record all observations, including vulnerabilities and areas for improvement. A detailed report, like a 50-point evaluation checklist, can offer a comprehensive overview of the evaluation results, guiding future procurement strategies. Furthermore, AI-powered systems enhance threat detection times from weeks to minutes, rendering them essential instruments in contemporary procurement evaluations.
By adhering to these steps, organizations can guarantee a thorough purchase product security audit in Mexico that efficiently detects vulnerabilities and enhances their procurement methods.
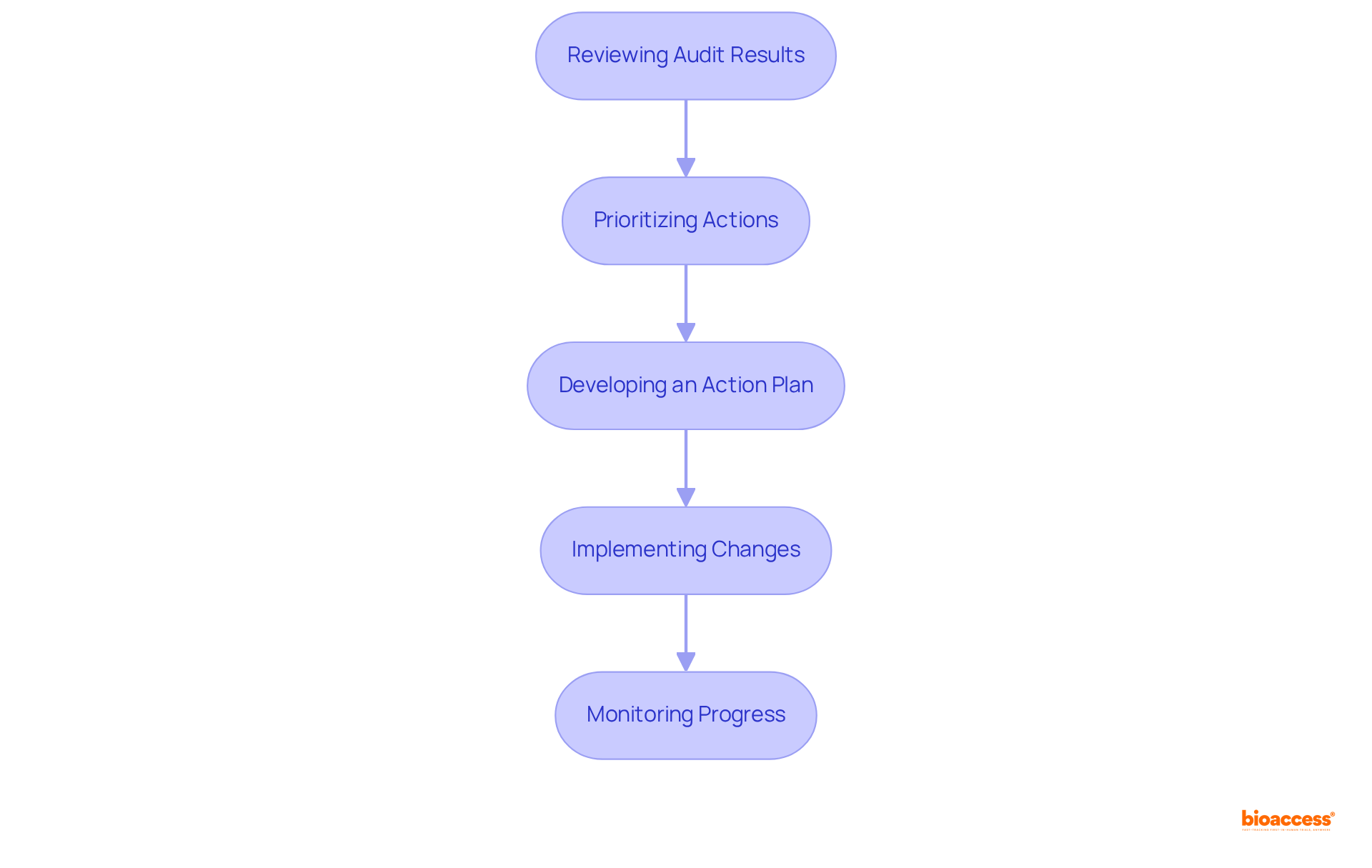
After completing a purchase product security audit in Mexico, it is essential to carefully examine the results and make necessary adjustments to enhance security and adherence. This process can be broken down into five essential steps:
Reviewing Audit Results: Begin by assessing the findings to pinpoint critical vulnerabilities and adherence issues that require immediate attention. According to a recent report, organizations that perform regular regulatory audits can save an average of $2.86 million.
Prioritizing Actions: Identify which issues demand urgent resolution and which can be addressed in a phased manner, ensuring that the most pressing risks are mitigated first. As noted by compliance expert Ayush Saxena, "Organizations are rapidly turning to compliance programs to build trust with clients and stakeholders, avoid fines and penalties, and build strong cybersecurity posture to protect sensitive data."
Developing an Action Plan: Formulate a comprehensive action plan that details how to tackle each identified issue, specifying timelines and assigning responsibilities to relevant team members. Utilizing tools like Xoralia can simplify this workflow by offering a centralized policy library and automation of policy tasks.
Implementing Changes: Execute the action plan by making necessary adjustments to policies, procedures, and protective measures, ensuring that all changes align with regulatory requirements. Establishing a formal incident response procedure can save organizations an average of $1.89 million, emphasizing the financial advantages of proactive regulatory measures.
Monitoring Progress: Continuously track the effectiveness of the implemented changes, making adjustments as necessary to maintain adherence and enhance protection. With 85% of organizations considering cybersecurity a high or very high risk, ongoing monitoring is essential to adapt to evolving threats.
By diligently following these steps, organizations can significantly improve their security posture and ensure adherence to regulatory standards, ultimately fostering a culture of compliance and trust.
A purchase product security audit in Mexico is an essential mechanism for organizations aiming to assess and enhance their procurement processes, ensuring compliance and protecting against vulnerabilities. By grasping the audit's purpose, organizations can effectively prioritize their security measures and take informed actions to safeguard their assets and reputation.
Key points throughout the article highlight the critical nature of:
Each step, from conducting interviews to analyzing findings, is integral to establishing a robust security framework. The insights shared underscore that regular audits not only reveal hidden risks but also cultivate a culture of accountability, ultimately leading to enhanced compliance and a stronger security posture.
Embracing the practice of conducting purchase product security audits transcends mere regulatory obligation; it represents a strategic advantage that can protect organizations from financial losses and reputational harm. As the procurement landscape evolves, maintaining vigilance and proactively implementing audit recommendations will empower organizations to effectively navigate challenges and uphold trust with stakeholders. Thus, prioritizing these audits is vital for any organization dedicated to excellence in procurement practices.
What is the purpose of a purchase product security audit in Mexico?
The purpose of a purchase product security audit in Mexico is to assess the security measures governing the procurement process of products. It identifies potential vulnerabilities that could lead to data breaches or regulatory issues, helping organizations prepare for compliance with local regulations while safeguarding their assets and reputation.
What are the key objectives of a purchase product security audit?
The key objectives include identifying vulnerabilities in the procurement process, ensuring conformity with relevant regulations and standards, and improving the organization's protective stance by implementing enhancements based on audit findings.
Why is it important to identify vulnerabilities in the procurement process?
Identifying vulnerabilities is crucial because it helps organizations pinpoint weaknesses that may be exploited. In 2023, 96% of US companies faced at least one fraud attempt, highlighting the urgent need for vigilance in procurement practices.
What are the regulatory requirements for conducting audits in Mexico?
Key regulatory requirements include the Federal Law on Protection of Personal Data, which mandates regular audits and safeguarding personal data; NOM Standards, which ensure product safety and quality; and ISO Standards, such as ISO 27001, which bolster adherence to security practices.
What are the potential penalties for non-compliance with the Federal Law on Protection of Personal Data?
Non-compliance can result in significant penalties, with fines reaching up to approximately USD 1.7 million for breaches.
How can organizations ensure they are compliant with the regulations?
Organizations are encouraged to engage legal experts or compliance officers to fully understand and implement all applicable regulations, especially in light of recent changes affecting compliance strategies.
What impact do regular security evaluations have on organizations?
Regular security evaluations help identify gaps in compliance and foster a culture of accountability and integrity within procurement teams, ultimately leading to a reduction in vulnerabilities and an increase in compliance rates.